Published: July 22, 2025
ForceTech Security & Governance Framework
Effective Date: July 22, 2025
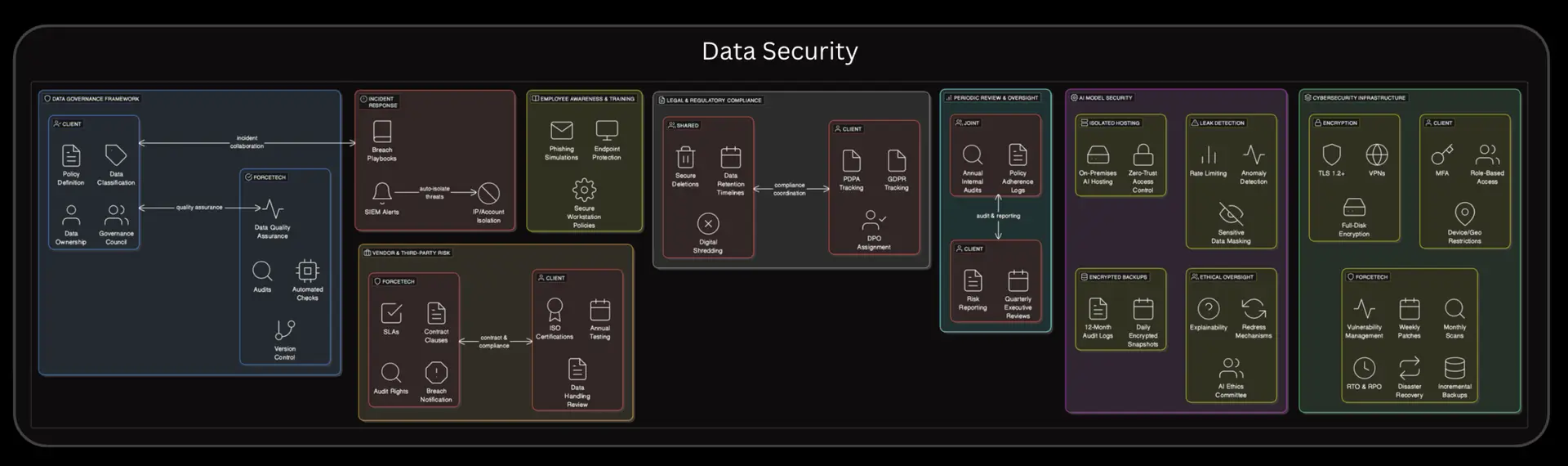
1. Data Governance Framework
Objective: Establish clear policies and processes to ensure the integrity, confidentiality, and availability of data.
1.1 Policy Definition [Client]
- Document standardized rules for data collection, storage, processing, and sharing.
- Classify data by sensitivity level:
- Public
- Internal
- Restricted
- Assign data ownership to relevant departments.
- Develop a Data Governance Council to review and approve new data practices.
1.2 Data Quality Assurance [ForceTech]
- Implement automated validation checks for completeness, accuracy, and consistency.
- Perform routine data audits and reconciliation.
- Record anomalies and corrective action logs.
- Introduce version control for critical datasets.
- Establish thresholds for acceptable data quality metrics.
2. AI Model Security
Objective: Protect proprietary AI models, datasets, and insights from unauthorized access or data leakage.
2.1 Leak Detection and Monitoring [ForceTech]
- Analyze model logs for anomalous patterns or scraping behavior.
- Trigger incident response for excessive or pattern-based queries (e.g., full customer records).
- Introduce rate-limiting and throttling mechanisms.
- Mask sensitive outputs during testing and logging.
2.2 Isolated Hosting [ForceTech]
- Host LLM and AI workloads on isolated, on-premises servers.
- Disable outbound internet access on LLM nodes.
- Segment AI infrastructure from general networks using VLANs and firewalls.
- Implement access controls based on zero trust principles.
2.3 Encrypted Backups & Audit Trails [ForceTech]
- Automate encrypted daily backups of AI models and datasets.
- Maintain 12-month logs capturing access metadata (user, timestamp, activity).
- Store backups in tamper-proof locations.
- Review audit logs weekly and flag anomalies.
3. Robust Cybersecurity Infrastructure
Objective: Prevent, detect, and mitigate security threats across systems and networks.
3.1 Data-in-Transit & At-Rest Encryption [ForceTech]
- Enforce HTTPS with TLS 1.2+ for all services.
- Use full-disk encryption on servers, storage, and model servers.
- Utilize end-to-end encryption for internal data pipelines.
- Implement VPN for remote workforce access.
3.2 Multi-Factor Authentication (MFA) [Client]
- Require MFA for all users.
- Apply Role-Based Access Control (RBAC).
- Perform quarterly access reviews and updates.
- Deny access from untrusted devices or geographies.
3.3 Patching & Vulnerability Management [ForceTech]
- Maintain updated software inventory.
- Enforce weekly patch cycles; deploy critical patches within 48 hours.
- Subscribe to vendor vulnerability bulletins.
- Conduct monthly vulnerability scans.
3.4 Disaster Recovery & Backups [ForceTech]
- Daily full and hourly incremental encrypted backups.
- Off-site storage using secure cloud vaults.
- Conduct quarterly recovery drills; document recovery runbooks.
- Define RTO (Recovery Time Objective) and RPO (Recovery Point Objective) for critical systems.
4. Vendor & Third-Party Risk Management
Objective: Ensure external parties meet organizational security standards.
4.1 Due Diligence & Certification [Client]
- Onboard vendors with ISO 27001 or equivalent certifications.
- Conduct annual vendor security and penetration testing.
- Evaluate vendor data handling practices via questionnaires.
- Review historical breaches or incidents involving vendors.
4.2 Contractual Safeguards [ForceTech]
- Define SLAs with response times for incidents, vulnerabilities, and outages.
- Include data handling clauses for Phitomas, Hatio, and any third-party API integrations.
- Mandate breach notification within 24 hours.
- Require right-to-audit clauses in contracts.
5. Employee Awareness & Training
Objective: Cultivate a security-first culture among all staff.
5.1 Phishing Simulations [Client]
- Conduct quarterly phishing awareness tests.
- Track success rates and follow up with personalized training.
- Maintain a leaderboard to encourage participation.
5.2 Secure Workstation Practices [Client]
- Enforce endpoint protection with licensed antivirus and automatic updates.
- Disable USB port access for data transfer unless approved.
- Enforce strong password policies and lock screens.
- Install local firewall and endpoint detection and response (EDR) tools.
6. Incident Response Plan
Objective: Respond effectively to minimize business and legal risks from breaches.
6.1 Breach Playbook [ForceTech]
- Clearly defined roles: IT → Legal → Executive escalation flow.
- Response stages: Detection → Containment → Eradication → Recovery → Review.
- Maintain emergency contact directory.
- Test breach simulation scenarios bi-annually.
6.2 Real-Time Alerting [ForceTech]
- Centralized log monitoring (SIEM) with threshold-based triggers.
- Notify SOC (Security Operations Center) via email and SMS for high-severity events.
- Integrate alerts with Slack, Teams, or incident response systems.
- Automate isolation of compromised accounts or IPs.
7. Ethical AI & Transparency
Objective: Ensure AI models are explainable, accountable, and trustworthy.
7.1 Feedback & Redress Mechanism [ForceTech]
- Provide in-app “Report Recommendation” feature.
- Feed back flagged cases into model retraining.
- Allow customers to request explanation of AI-based decisions.
- Display disclaimers for automated decision-making modules.
7.2 AI Ethics Committee [ForceTech]
- Multi-functional team (Tech, Legal, Ops) meets monthly.
- Review AI usage for bias, transparency, and fairness.
- Require documented committee approval before production rollout of impactful features.
- Maintain an AI risk register.
8. Legal and Regulatory Compliance
Objective: Align practices with applicable data protection and cybersecurity laws.
8.1 Legal Mandates Tracking [Client]
- Track local regulations: PDPA (Malaysia), GDPR (if applicable), etc.
- Maintain records of user consent for data usage.
- Assign Data Protection Officer (DPO) with regulatory oversight.
8.2 Data Retention & Deletion Policy [ForceTech + Client]
- Define and document data retention timelines by data type.
- Enforce secure deletion for expired or revoked data (e.g., customer deletion requests).
- Use digital shredding methods for critical data.
- Log all deletion activities and review monthly.
9. Periodic Review & Governance Oversight
Objective: Ensure ongoing relevance and effectiveness of security practices.
9.1 Executive Review [Client]
- Present quarterly security reports to the Board and CTO.
- Document risk register and mitigation updates.
- Highlight emerging threats and industry benchmarks.
9.2 Internal Audit [Client + ForceTech]
- Perform annual security and governance audits.
- Report findings with actionable timelines and responsible owners.
- Audit trail must include policy adherence, exception logs, and corrective actions.
